Rediscover Your Network 👨💻
Are you concerned that your current security infrastructure may not accurately detect today’s sophisticated attacks? Do you have the operational visibility to understand how applications (traditional and web-based) are truly being utilized on your network? Is your current security solution able to sustain present-day throughput demands despite increased traffic volume (perhaps due to cloud based storage, big data analytics or increased web usage)? If you are asking any of these questions, the Cyber Threat Assessment is for you! Validate your network’s security effectiveness, user productivity, and utilization by enlisting expert guidance.
Security and Threat Prevention
How effective is your current network security solution?
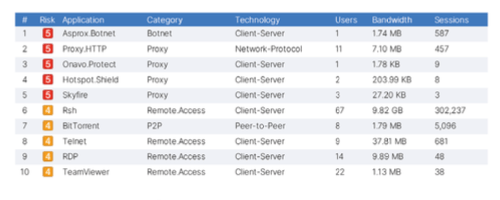
Learn more about application vulnerabilities that are attacking your network, which malware/botnets were detected and even pinpoint “at risk” devices within your network. Make sure your existing security solution isn’t letting anything slip through the cracks by leveraging award-winning content security.
User Productivity
How are applications and web resources used within your network?
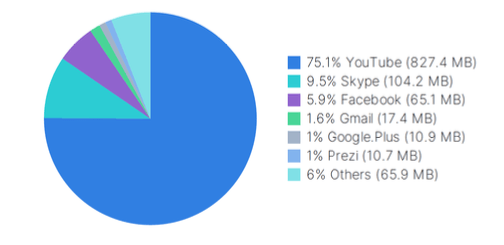
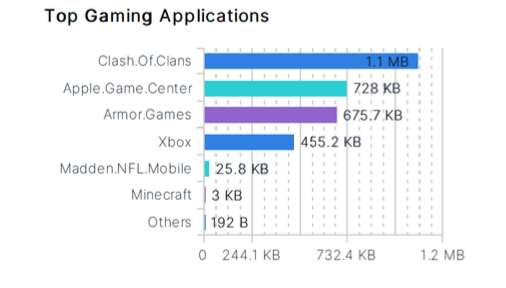
Discover how cloud-based IaaS/SaaS, peer to peer, gaming, and other application subcategories are being utilized within your network. Verify that usage of your traditional client-server and web-based applications are operating in accordance with your corporate use policies.
Network Utilization & Performance
How should your network security solution be optimized for performance?
Find out more about your throughput, session and bandwidth requirements during peak hours. Ensure your security solution is sized and optimized properly based on your actual usage. Obtaining a Cyber Threat Assessment Report will give you unmatched insight into your current security posture and network activity. Learn more about your network by requesting an assessment today!
Digital Transformation
Tips, Tricks & Tech Trends
Stay Informed!
All Rights Reserved | Fearless IT • Privacy Policy • Terms of Service • Disclaimer



